The BlueNoroff cryptocurrency hunt is still on
SecureList
JANUARY 13, 2022
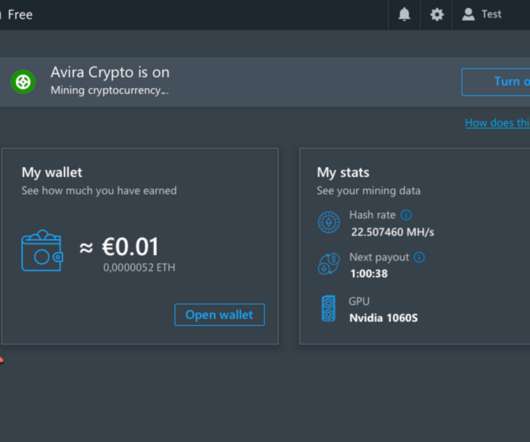
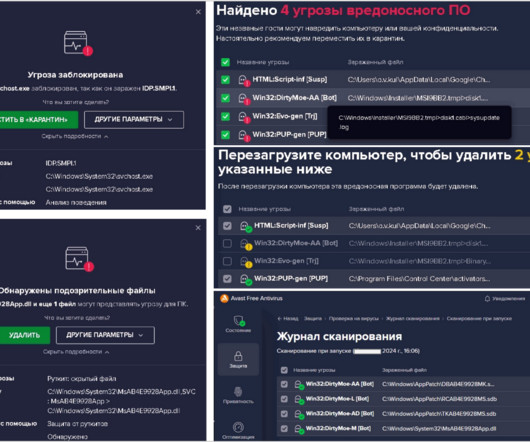
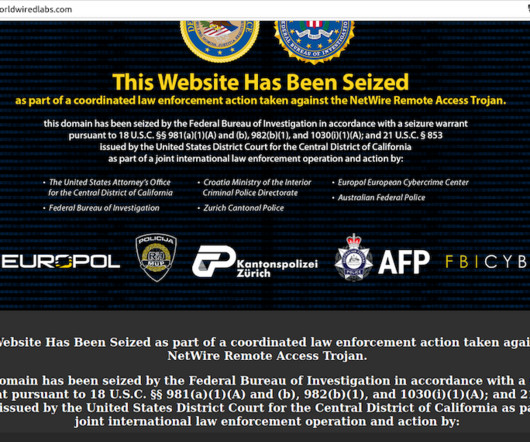
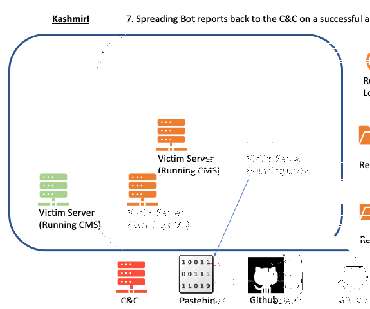
Also, we have previously reported on cryptocurrency-focused BlueNoroff attacks. It appears that BlueNoroff shifted focus from hitting banks and SWIFT-connected servers to solely cryptocurrency businesses as the main source of the group’s illegal income. Instead, they can rely on regular macro-enabled documents or older exploits.









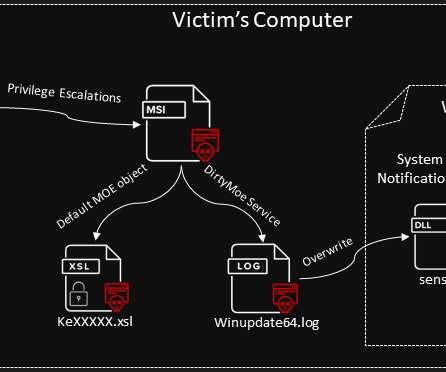





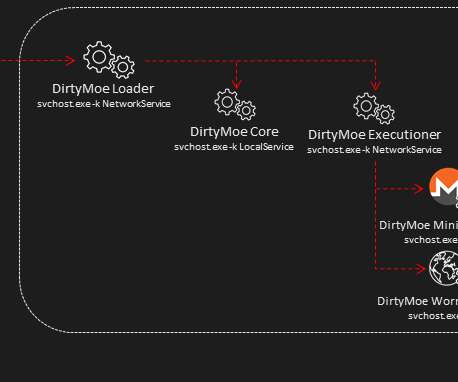

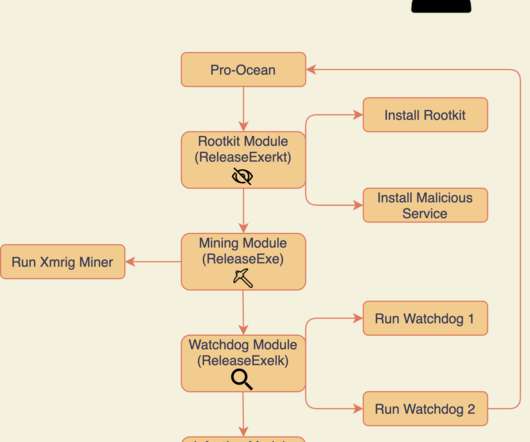






















Let's personalize your content