InvisiMole group targets military sector and diplomatic missions in Eastern Europe
Security Affairs
JUNE 18, 2020
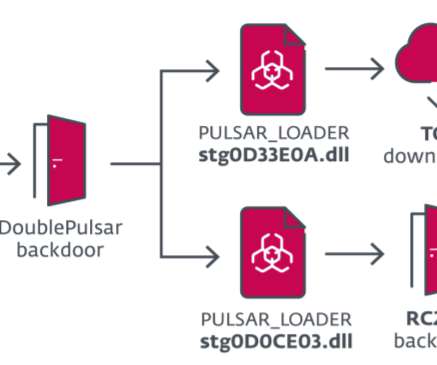
The group was first spotted by ESET in 2018, when the experts detected a sophisticated piece of spyware, tracked as InvisiMole, used in targeted attacks in Russia and Ukraine in the previous five years. Experts also observed attackers using a DNS downloader that was designed for long-term, covert access to the target machine.
















Let's personalize your content