My Philosophy and Recommendations Around the LastPass Breaches
Daniel Miessler
DECEMBER 24, 2022
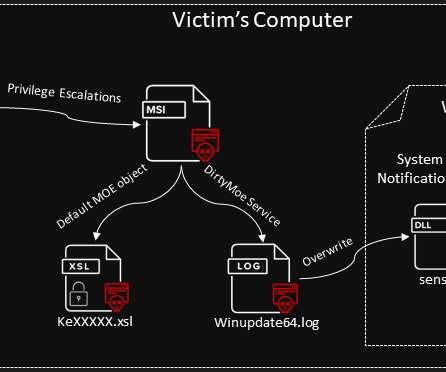
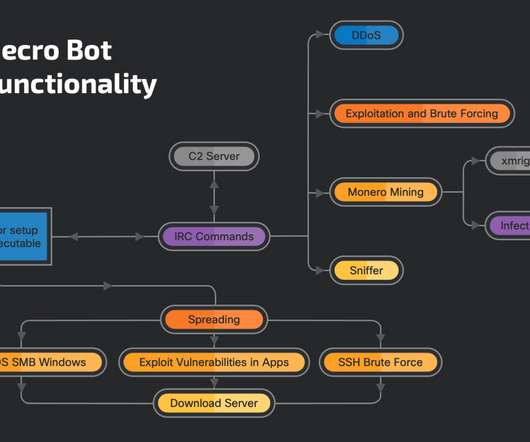
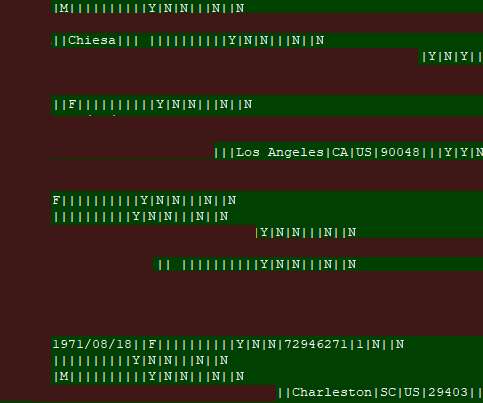
If you follow Information Security at all you are surely aware of the LastPass breach situation. After initiating an immediate investigation, we have seen no evidence that this incident involved any access to customer data or encrypted password vaults. So basically: Minor incident, but no customer data or vaults were lost.







































Let's personalize your content