Tricky Phish Angles for Persistence, Not Passwords
Krebs on Security
JANUARY 7, 2020
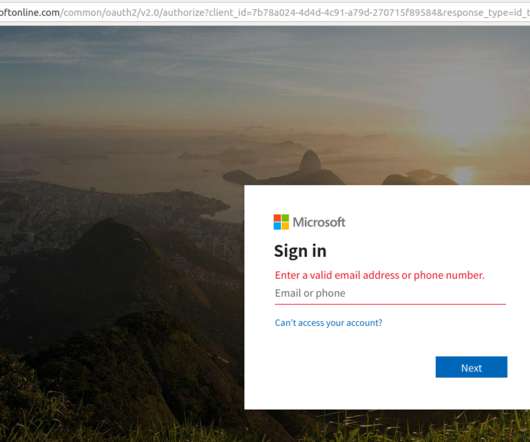
Late last year saw the re-emergence of a nasty phishing tactic that allows the attacker to gain full access to a user’s data stored in the cloud without actually stealing the account password. I look at this and think, would I be more likely to type my password into a box or more likely to click a button that says ‘okay’?”























Let's personalize your content