Russia-linked InvisiMole APT targets state organizations of Ukraine
Security Affairs
MARCH 21, 2022
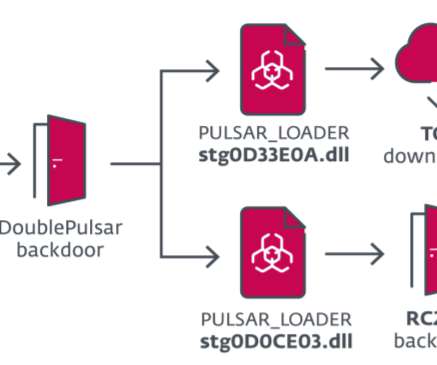
Then the backdoor contacts the command-and-control (C2) server to downloads and executes other malicious payloads, including the TunnelMole, malware that abuses the DNS protocol to establish a tunnel for malicious purposes, and RC2FM and RC2CL. SecurityAffairs – hacking, InvisiMole). ” reads the advisory published by CERT-UA.


















Let's personalize your content