Fileless SockDetour backdoor targets U.S.-based defense contractors
Security Affairs
FEBRUARY 26, 2022
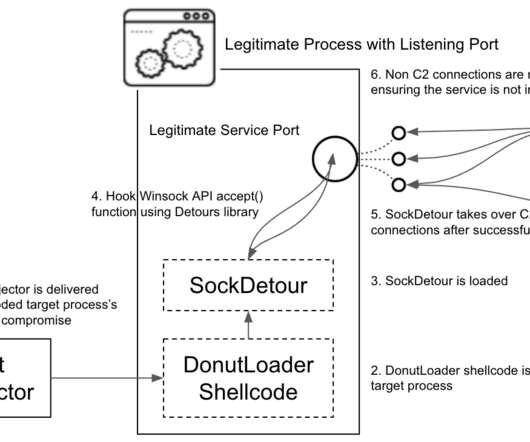
According to the experts, the SockDetour backdoor has been in the wild since at least July 2019. SockDetour serves as a backup fileless Windows backdoor in case the primary one is removed. based defense contractors. “It is difficult to detect, since it operates filelessly and socketlessly on compromised Windows servers.”




























Let's personalize your content