NSA warns Russia-linked APT group is exploiting Exim flaw since 2019
Security Affairs
MAY 28, 2020
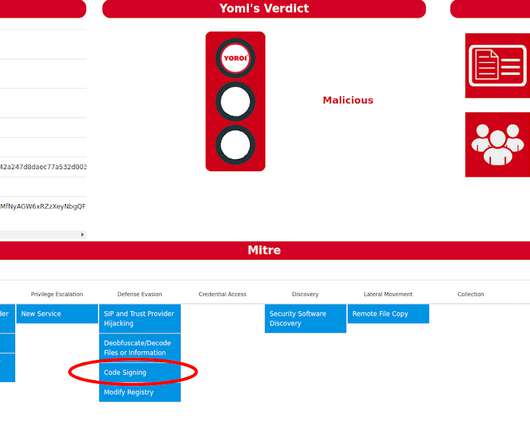
National Security Agency (NSA) is warning that Russia-linked APT group tracked Sandworm Team has been exploiting a critical vulnerability (CVE-2019-10149) in the Exim mail transfer agent (MTA) software since at least August 2019. The CVE-2019-10149 flaw, aka “The Return of the WIZard,” affects versions 4.87





















Let's personalize your content