DirtyMoe botnet infected 100,000+ Windows systems in H1 2021
Security Affairs
JUNE 22, 2021
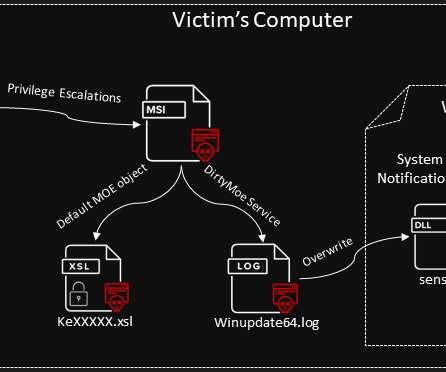
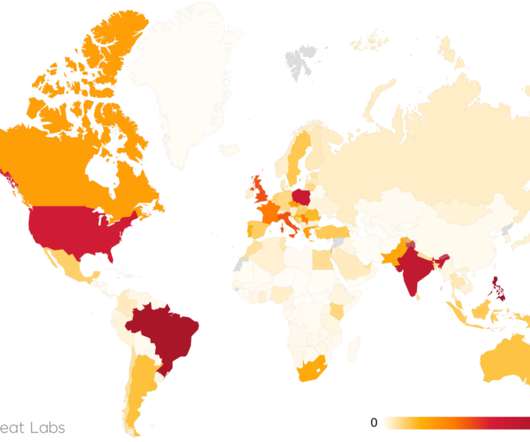
DirtyMoe is a Windows botnet that is rapidly growing, it passed from 10,000 infected systems in 2020 to more than 100,000 in the first half of 2021. Experts pointed out that the number of infected systems could be far greater because data provided by AVAST are only related to systems running their antivirus solution.





























Let's personalize your content