Using a Mythic agent to optimize penetration testing
SecureList
MAY 13, 2025
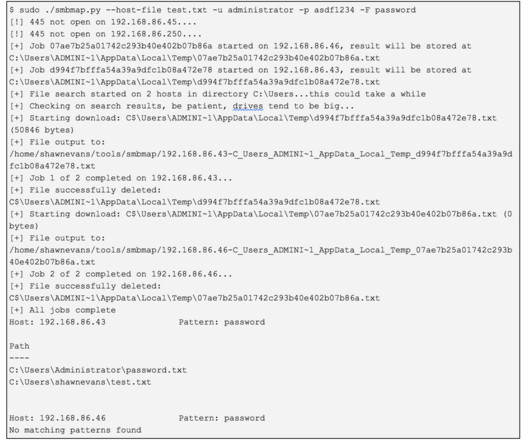
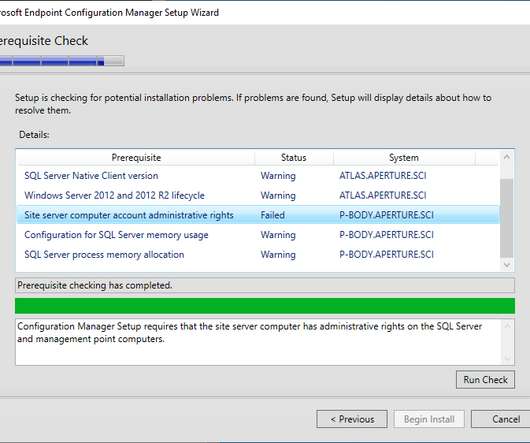
Our company’s deep expertise means we can study these tools to implement best practices in penetration testing. The text is written for educational purposes only and intended as an aid for security professionals who are conducting penetration testing with the system owner’s consent.













































Let's personalize your content