12 Online Resolutions for 2021
Adam Levin
DECEMBER 16, 2020
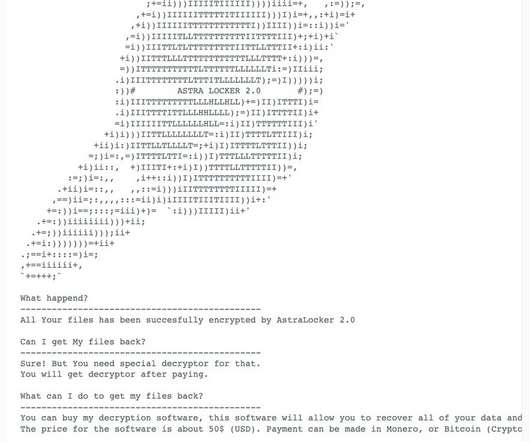
Here are 12 New Year Resolutions for a safer and more secure digital you in 2021: Think before you click that email link: 2020 was a record-breaking year for ransomware, malware, and phishing , and many, if not most of these attacks were launched with the click on a link in an email. That’s always the case when it comes to cybersecurity.














































Let's personalize your content