Attacks Escalating Against Linux-Based IoT Devices
eSecurity Planet
JANUARY 20, 2022
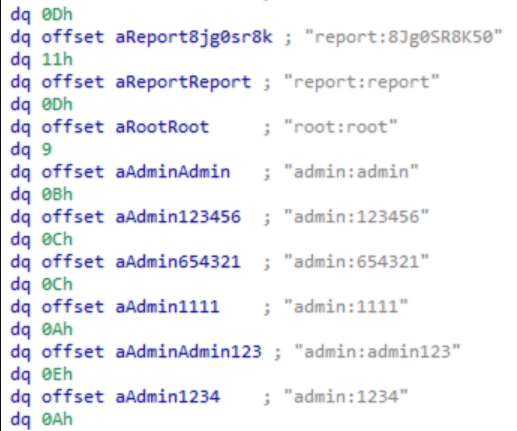
Incidents of malware targeting Linux-based Internet of Things (IoT) devices jumped by more than a third in 2021, with three malware families the primary drivers behind the increase. There was a 10-fold increase in the number of samples of Mozi found in the wild, Mihai Maganu, a threat researcher at CrowdStrike, wrote in a blog post.


























Let's personalize your content