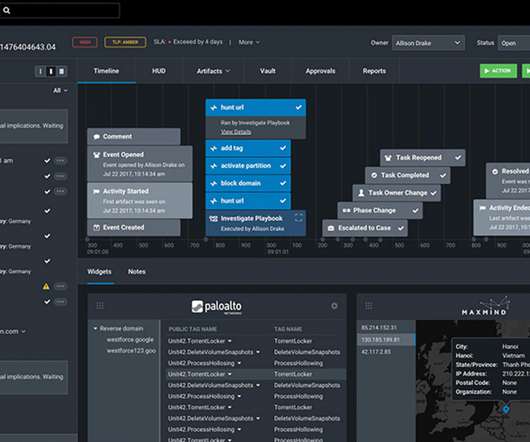
Top Security Orchestration, Automation and Response (SOAR) Solutions for 2022
eSecurity Planet
MARCH 16, 2022
And as cyber attackers become ever more sophisticated, so too have the technologies and tools that companies must buy to address rising threats, such as IDPS , UEBA , threat intelligence , patch management , encryption , DLP , DDoS protection , vulnerability management , and even mobile security management.















Let's personalize your content