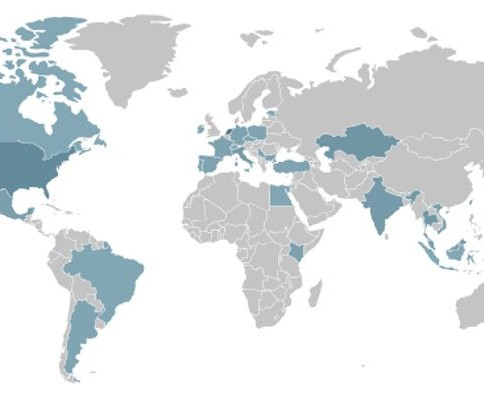
Experts warn of a surge in activity associated FICORA and Kaiten botnets
Security Affairs
DECEMBER 27, 2024
Some of the vulnerabilities exploited by the botnets are CVE-2015-2051 , CVE-2019-10891 , CVE-2022-37056 , and CVE-2024-33112. It first terminates processes with the same file extension as “FICORA” and then downloads and executes the malware targeting multiple Linux architectures.































Let's personalize your content