APT group exploited Output Messenger Zero-Day to target Kurdish military operating in Iraq
Security Affairs
MAY 13, 2025
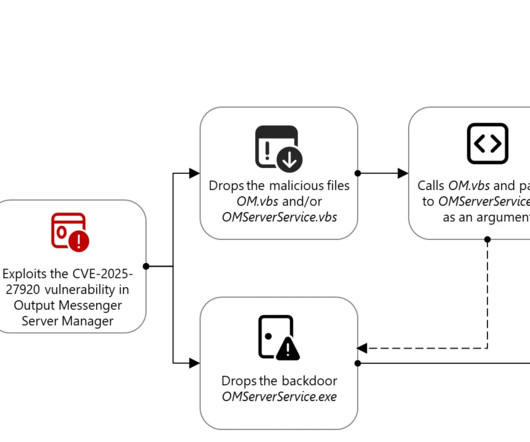
A Trkiye-linked group used an Output Messenger zero-day to spy on Kurdish military targets in Iraq, collecting user data since April 2024. Between 2017 and 2019, the APT group mainly used DNS hijacking in its campaigns. Marbled Dust exploited CVE-2025-27920 after likely stealing credentials via DNS hijacking or typo-squatting.





















Let's personalize your content