New Mirai botnet targets TBK DVRs by exploiting CVE-2024-3721
Security Affairs
JUNE 9, 2025
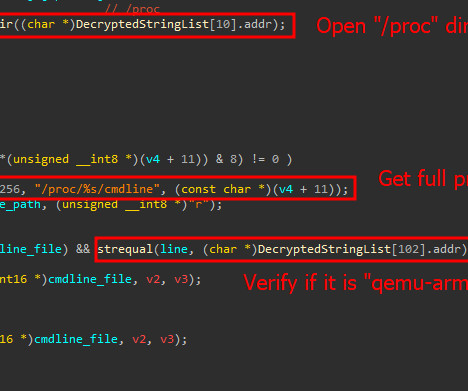
A new variant of the Mirai botnet exploits CVE-2024-3721 to target DVR systems, using a new infection method. Researchers from Russian cybersecurity firm Kaspersky discovered a new variant of the Mirai botnet that exploits a command injection vulnerability ( CVE-2024-3721 ) in TBK DVR-4104 and DVR-4216 digital video recording devices.

























Let's personalize your content