SOC 2025: Making Sense of Security Data
Security Boulevard
FEBRUARY 8, 2022
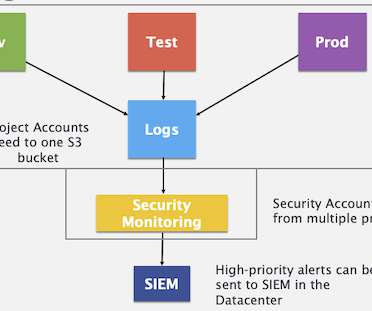
As we consider what the SOC will look like in 2025 , given the changing attack surface and available skills base, we’ve got to face reality. For modern infrastructures (read cloud and DevOps), we generally recommend a cascading log architecture , where all of the data is aggregated within the application stack. Mike Rothman. (0)








































Let's personalize your content