Elevate Cybersecurity Resilience With PCI-DSS 4.0
Security Boulevard
MARCH 22, 2023
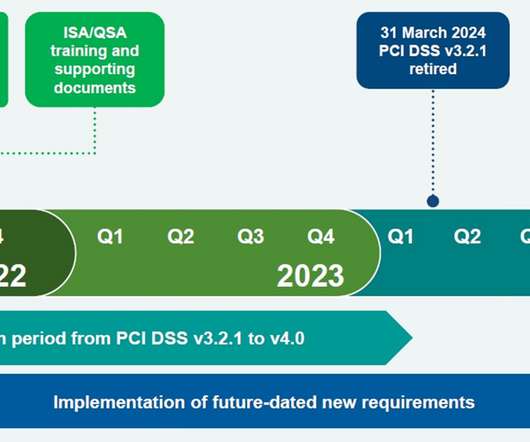
Earlier this year, the PCI Security Standards Council revealed version 4.0 of their payment card industry data security standard (PCI-DSS). until March 2025, this update is their most transformative to date and will require most businesses to assess (and likely upgrade) complex security processes and.





























Let's personalize your content