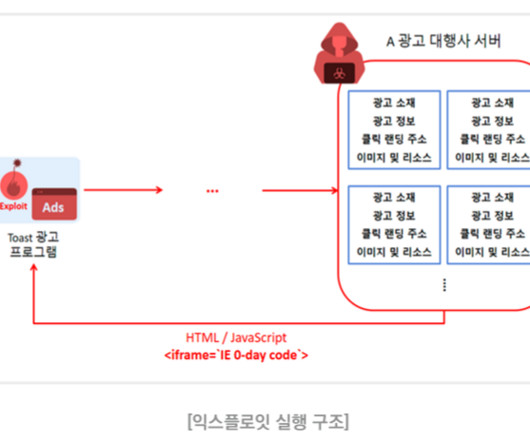
North Korea-linked APT37 exploited IE zero-day in a recent attack
Security Affairs
OCTOBER 19, 2024
APT37 has been active since at least 2012 , it made the headlines in early February 2028, when researchers revealed that the APT group leveraged a zero-day vulnerability in Adobe Flash Player to deliver malware to South Korean users.






















Let's personalize your content