Tracking the Cost of Quantum Factoring
Google Security
MAY 23, 2025
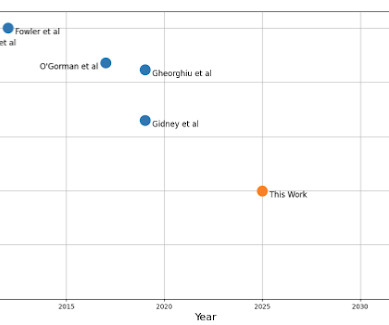
Yesterday, we published a preprint demonstrating that 2048-bit RSA encryption could theoretically be broken by a quantum computer with 1 million noisy qubits running for one week. Google has therefore been encrypting traffic both in Chrome and internally , switching to the standardized version of ML-KEM once it became available.


























Let's personalize your content