Video: How Hackers Steal Your Cookies & How to Stop Them
eSecurity Planet
NOVEMBER 6, 2024
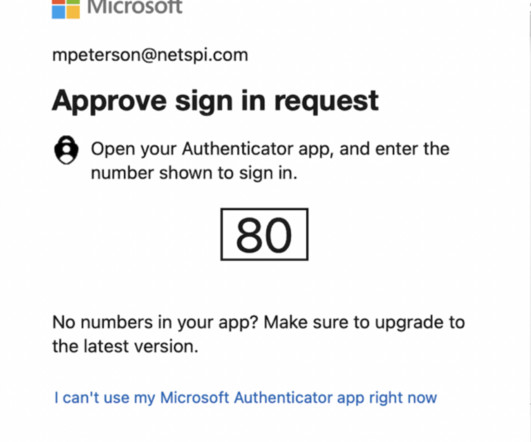
Don’t forget: You can read the full article on eSecurity Planet. They could even conceal dangerous malware in photos or links on secure websites you visit, and a single click can activate the code, even overcoming multifactor authentication. In this video, we’ll show you how to stay safe. What Are Cookies?































Let's personalize your content