Verizon's 2025 DBIR: Threats Are Faster, Smarter, and More Personal
SecureWorld News
APRIL 23, 2025
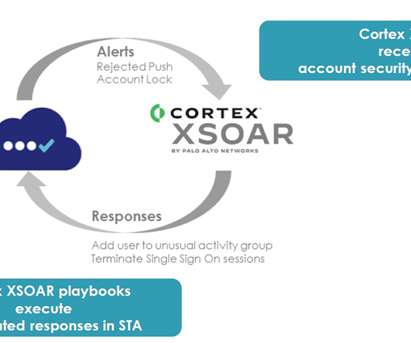
The most effective controls combine microsegmentation with strong authentication and adaptive access and behavioral analytics. Techniques like chaos engineering for security testing, which stress-test defenses in unpredictable ways, and machine learningdriven anomaly detection offer fresh layers of defense.


























Let's personalize your content