How to Identify and Avoid Holiday Phishing Scams
Identity IQ
AUGUST 31, 2023
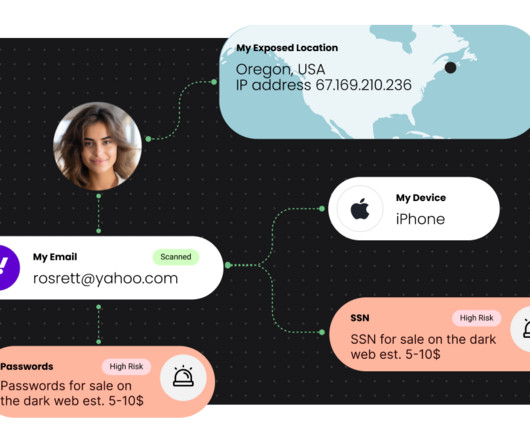
How to Identify and Avoid Holiday Phishing Scams IdentityIQ The holiday season brings joy, celebrations, and… a surge in online scams. Holiday phishing scams are an ongoing issue that ramps up when folks are feeling the most festive. About three-quarters of American consumers have encountered some form of holiday-related scam.







































Let's personalize your content