Akira ransomware received $42M in ransom payments from over 250 victims
Security Affairs
APRIL 21, 2024
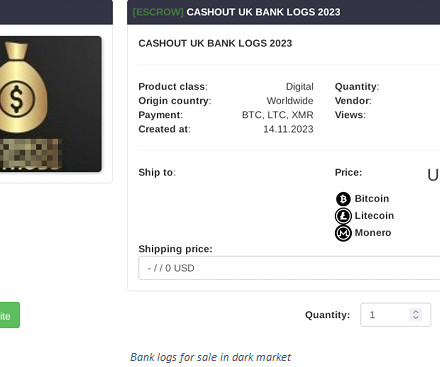
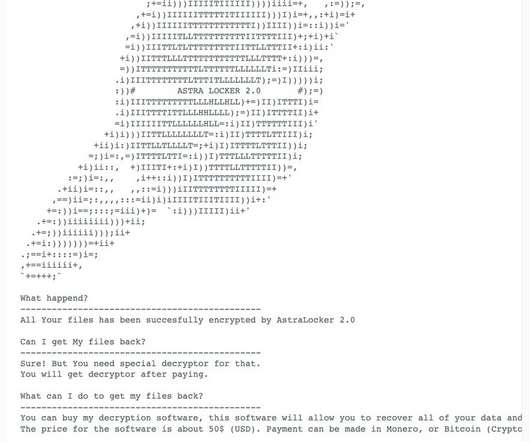
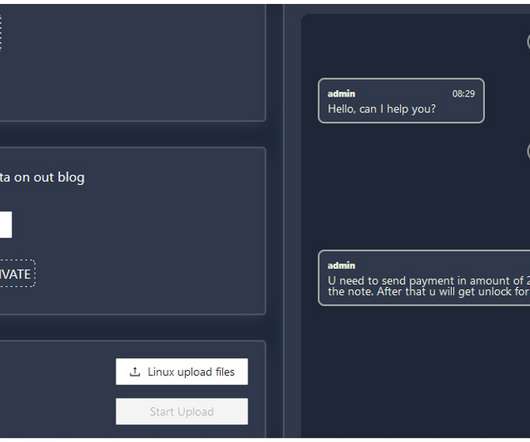
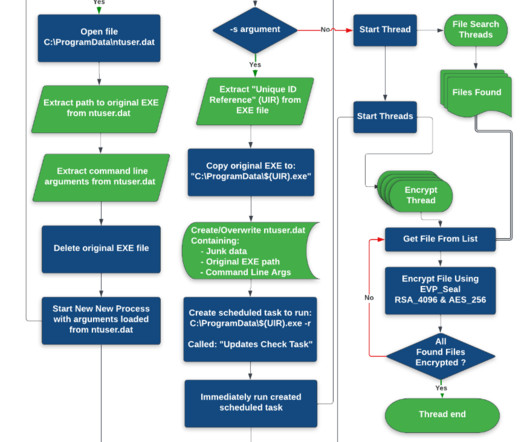
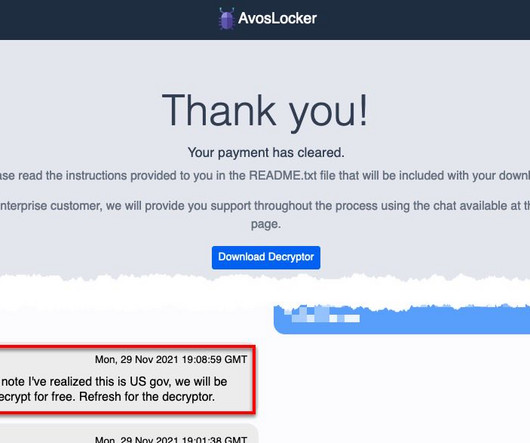
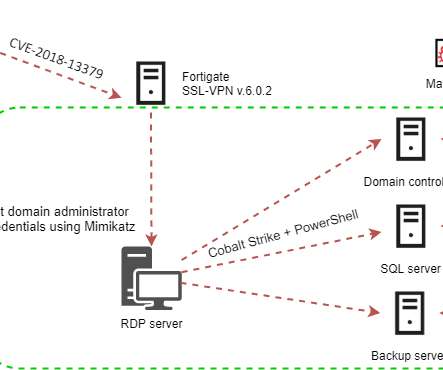
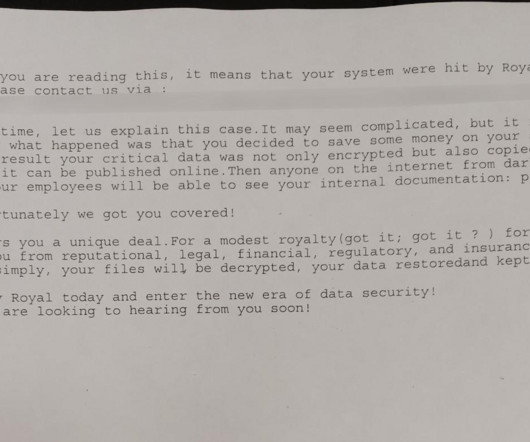
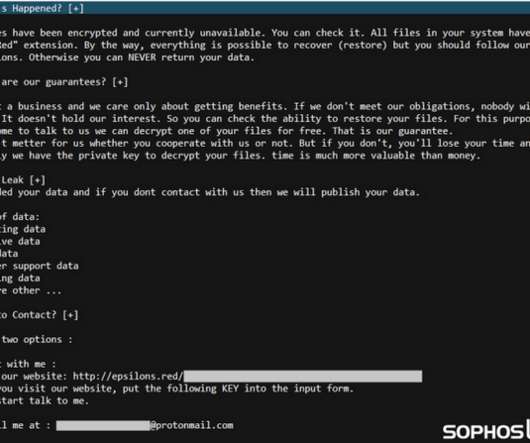
The Akira ransomware operators implement a double extortion model by exfiltrating victims’ data before encrypting it. Earlier versions of the ransomware were written in C++ and the malware added the.akira extension to the encrypted files. In some attacks, threat actors created an administrative account named itadm.








































Let's personalize your content