Talos wars of customizations of the open-source info stealer SapphireStealer
Security Affairs
SEPTEMBER 1, 2023
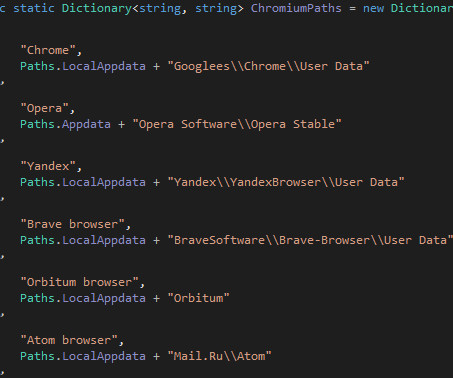
SapphireStealer allows operators to gather system data (i.e. IP address, hostname, screen resolution, OS version, CPU architecture, ProcessorId, and GPU information), and steal various browser credential databases and files that may contain sensitive user information. ” continues the report.




























Let's personalize your content