Social Engineering: Definition, Types, Detection & Prevention
Spinone
NOVEMBER 12, 2020
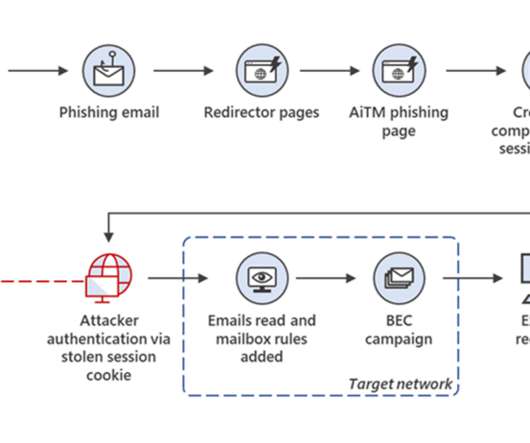
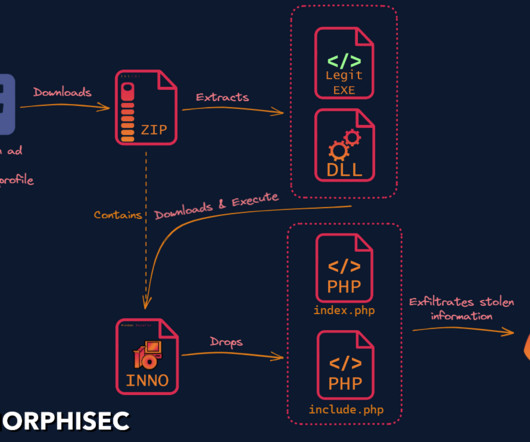
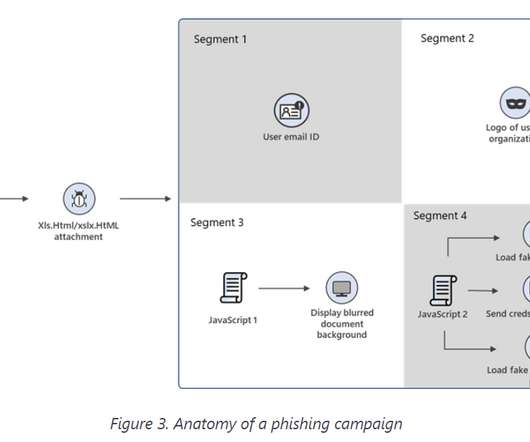
What is social engineering? Social engineering is a manipulative technique used by criminals to elicit specific actions in their victims. Social engineering is seldom a stand-alone operation. money from a bank account) or use it for other social engineering types.













































Let's personalize your content