Three Top Russian Cybercrime Forums Hacked
Krebs on Security
MARCH 4, 2021
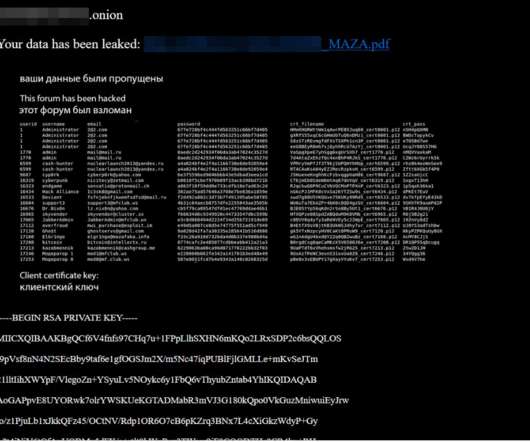
Over the past few weeks, three of the longest running and most venerated Russian-language online forums serving thousands of experienced cybercriminals have been hacked. At the top of a 35-page PDF leaked online is a private encryption key allegedly used by Maza administrators. The database also includes ICQ numbers for many users.








































Let's personalize your content