How (and Why) to Take Full Advantage of Apple’s New Advanced Data Protection Feature
Security Boulevard
DECEMBER 27, 2022
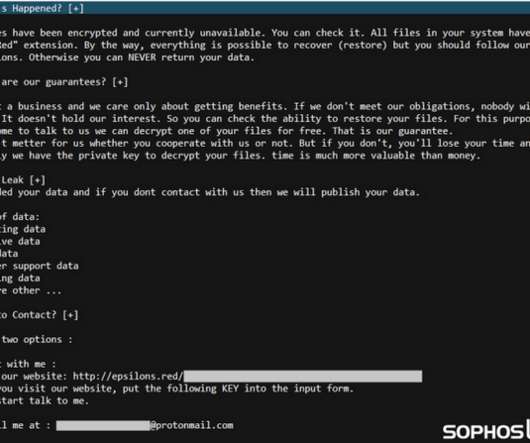
update, Apple introduced “Advanced Data Protection,” which finally introduced end-to-end encryption (E2EE) for most items backed up or stored in iCloud. Device backups. Enabling end-to-end encryption (Advanced Data Protection for iCloud). encrypted email providers. With the iOS 16.2 Safari Bookmarks. TABLE OF CONTENTS.















































Let's personalize your content