New Leak Shows Business Side of China’s APT Menace
Krebs on Security
FEBRUARY 22, 2024
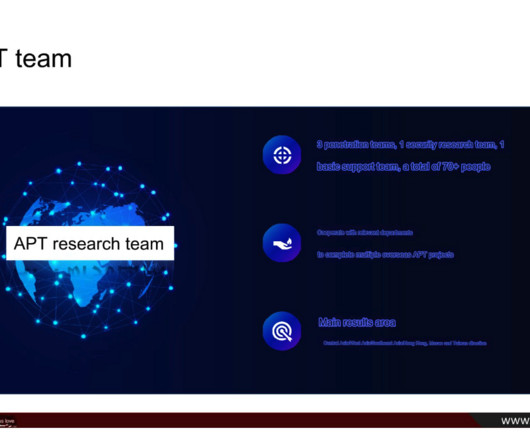
i-SOON’s “business services” webpage states that the company’s offerings include public security, anti-fraud, blockchain forensics, enterprise security solutions, and training. Danowski said that in 2013, i-SOON established a department for research on developing new APT network penetration methods.




















Let's personalize your content