Navy Insider Threat Bust: Encryption, Social Engineering, and Crypto
SecureWorld News
OCTOBER 12, 2021
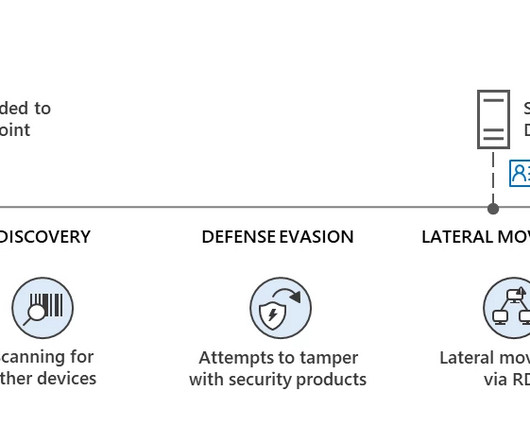
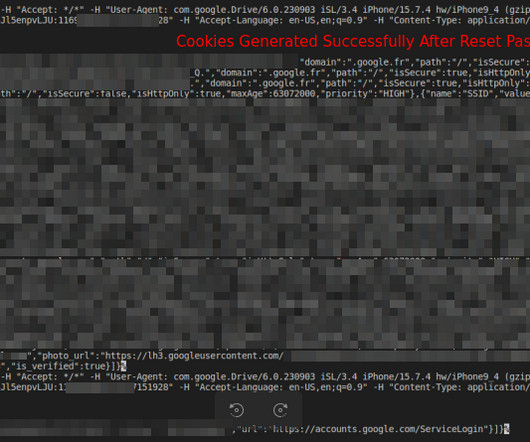
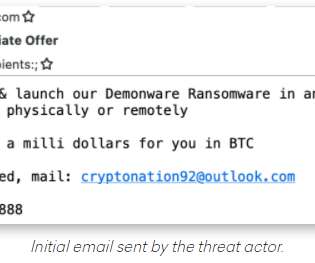
A Nuclear Engineer for the U.S. SecureWorld News just analyzed dozens of pages of court documents to understand this story of the Naval Engineer—an insider—who is accused of going rogue in a high-tech and high-stakes operation. Tools involved digital media, encrypted communication, cryptocurrency, and secret data handoffs.









































Let's personalize your content