Protecting Yourself from Identity Theft
Schneier on Security
MAY 6, 2019
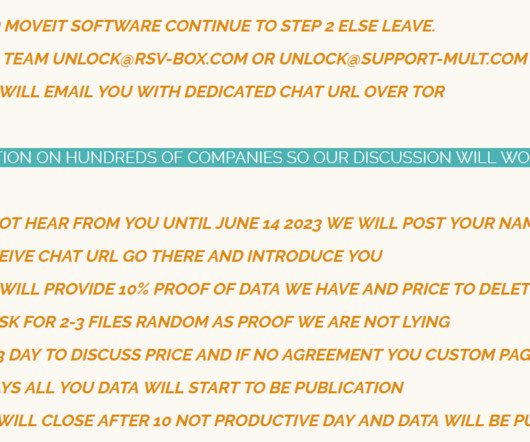
They obtained the data by hacking any one of the hundreds of companies you entrust with the data -- and you have no visibility into those companies' security practices, and no recourse when they lose your data. Enable two-factor authentication for all important accounts whenever possible. They have your address and phone number.













































Let's personalize your content