Task scams: Why you should never pay to get paid
We Live Security
JULY 4, 2025
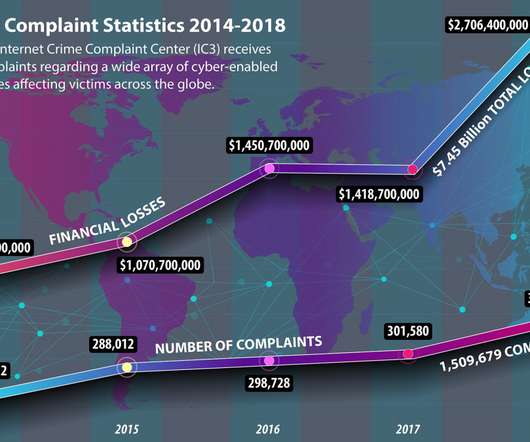
Here’s how to avoid getting played by gamified job scams. In 2024 alone, employment scams reported to the FBI made fraudsters over $264 million. Many of these are so-called “task scams,” where victims are actually tricked into paying a “deposit” in order to get paid. It might sound unbelievable.







































Let's personalize your content