Elevating Your Defenses with NetSPI’s Updated Social Engineering Solutions
NetSpi Executives
NOVEMBER 7, 2023
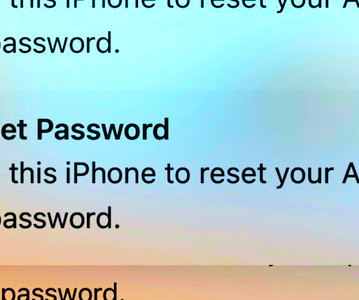
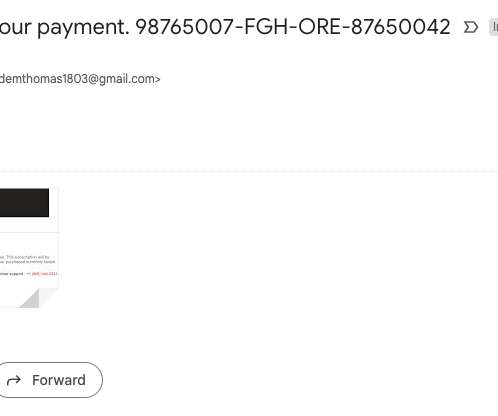
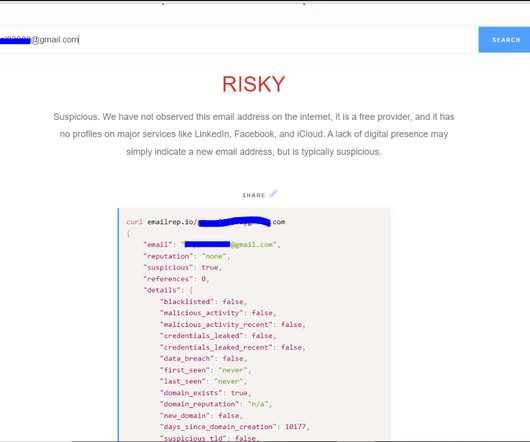
Although many companies are adding new processes, technologies, and training materials to combat this, employees continue to fall victim to phishing, vishing, and other forms of social engineering attacks. For further information on each of our unique Social Engineering Pentesting solutions, check out our data sheet or contact us.














































Let's personalize your content