Ragnar Locker ransomware gang advertises Campari hack on Facebook
Security Affairs
NOVEMBER 11, 2020
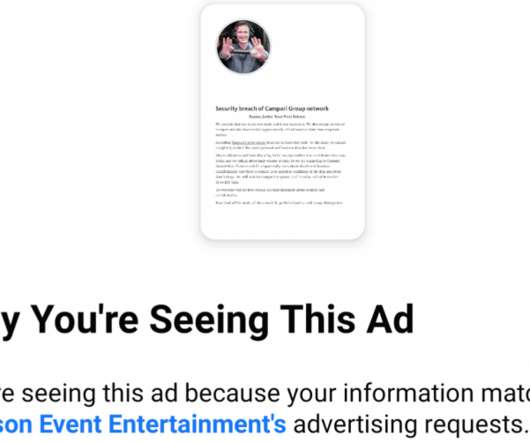
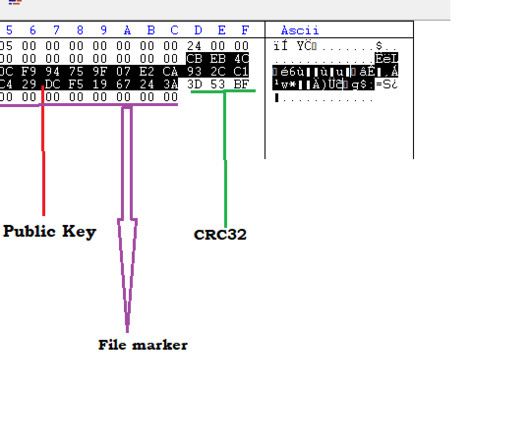
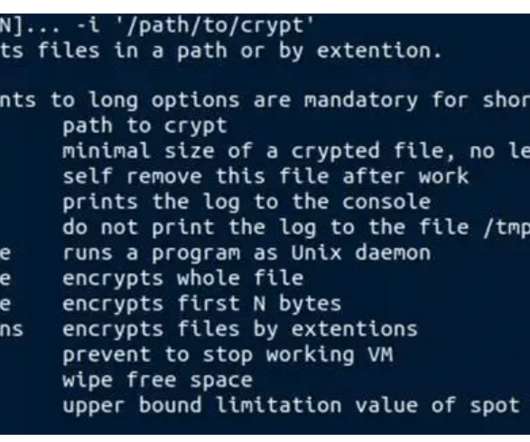
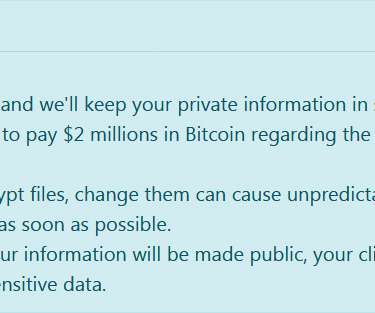
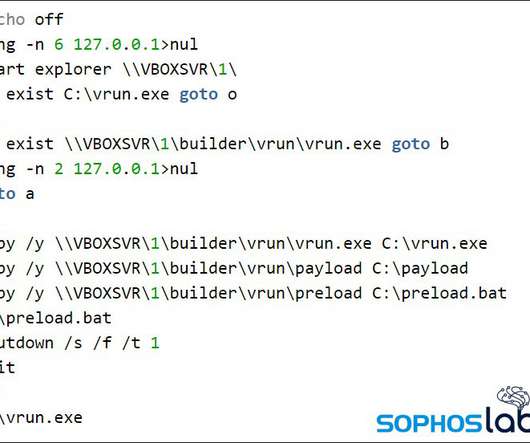
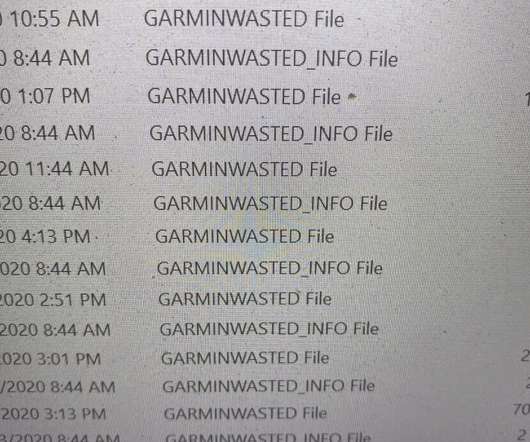
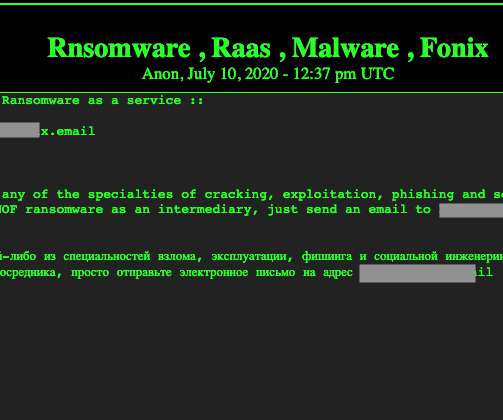
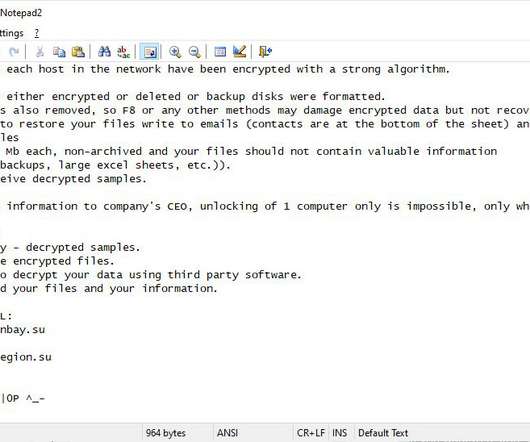
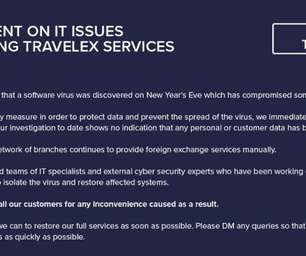
Ragnar Locker Ransomware operators have started to run Facebook advertisements to force their victims into paying the ransom. In November 2019, ransomware operators have started adopting a new double-extortion strategy first used by the Maze gang that sees threat actors also stealing unencrypted files before encrypting infected systems.


























Let's personalize your content