Using Google Search to Find Software Can Be Risky
Krebs on Security
JANUARY 25, 2024
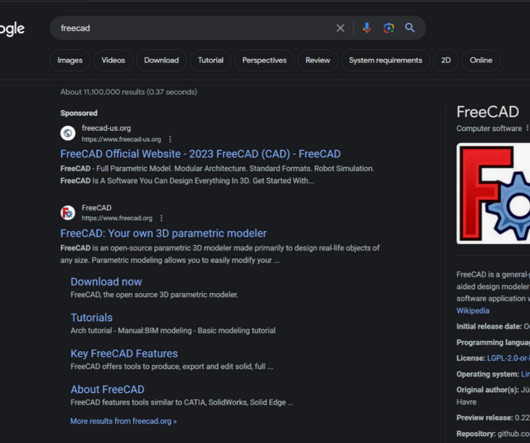
For example, a Google search earlier this week for the free graphic design program FreeCAD produced the following result, which shows that a “Sponsored” ad at the top of the search results is advertising the software available from freecad-us[.]org. million advertiser accounts. Google says it removed 5.2














Let's personalize your content