Almost Half of All Chrome Extensions Are Potentially High-Risk
eSecurity Planet
NOVEMBER 29, 2022
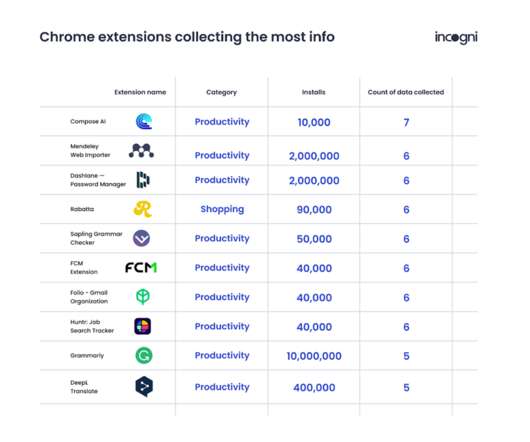
In a recent study of 1,237 Chrome extensions with a minimum of 1,000 downloads, Incogni researchers found that nearly half ask for permissions that could potentially expose personally identifiable information (PII), distribute adware and malware , or even log everything users do online, including accessing passwords and financial data.











Let's personalize your content