Malvertising Is a Cybercrime Heavyweight, Not an Underdog
SecureWorld News
MARCH 29, 2024
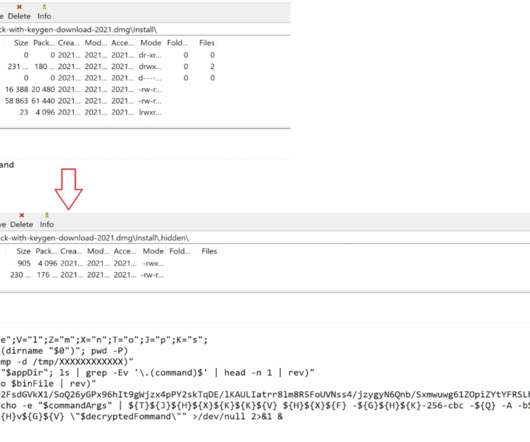
At its core, this tactic revolves around gaming the trust users put in reputable internet services, including search engines, and the familiarity they have with online advertising per se. This ends up executing sketchy code that installs viruses, ransomware, spyware, or adware behind the victim's back.












Let's personalize your content