Mobile malware evolution in 2024
SecureList
MARCH 3, 2025
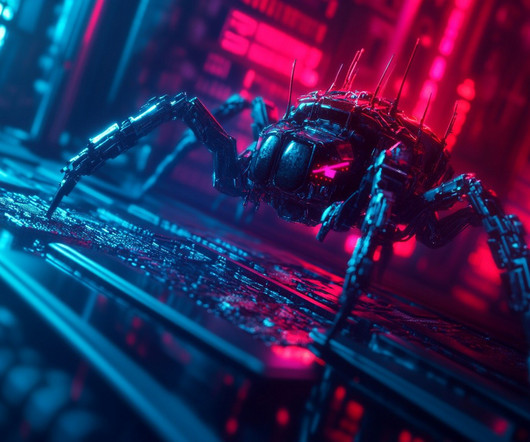
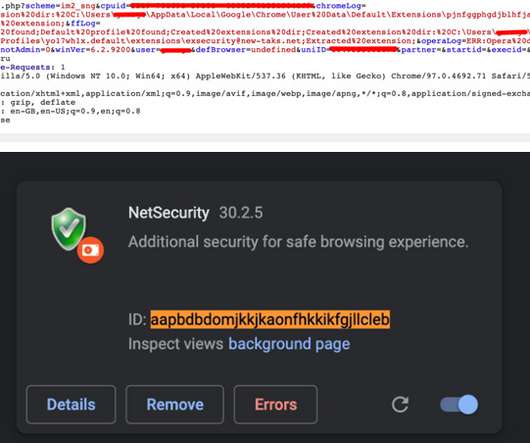
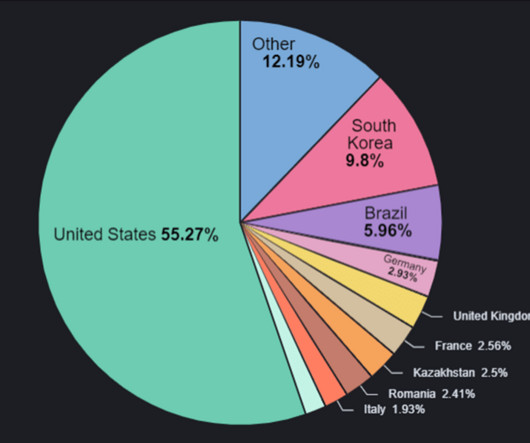
million attacks involving malware, adware or unwanted mobile software were prevented. Adware, the most common mobile threat, accounted for 35% of total detections. million malicious and potentially unwanted installation packages were detected, almost 69,000 of which associated with mobile banking Trojans.










































Let's personalize your content