Chinese hackers exploited a Trend Micro antivirus zero-day used in Mitsubishi Electric hack
Security Affairs
JANUARY 25, 2020
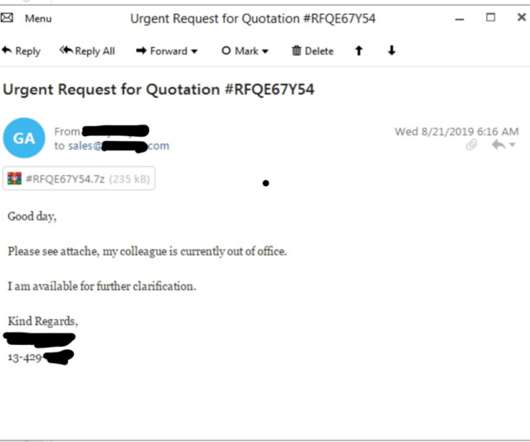
Chinese hackers have exploited a zero-day vulnerability the Trend Micro OfficeScan antivirus in the recently disclosed hack of Mitsubishi Electric. The two media outlets attribute the cyber attack to a China-linked cyber espionage group tracked as Tick (aka Bronze Butler ). An attempted attack requires user authentication.”













































Let's personalize your content