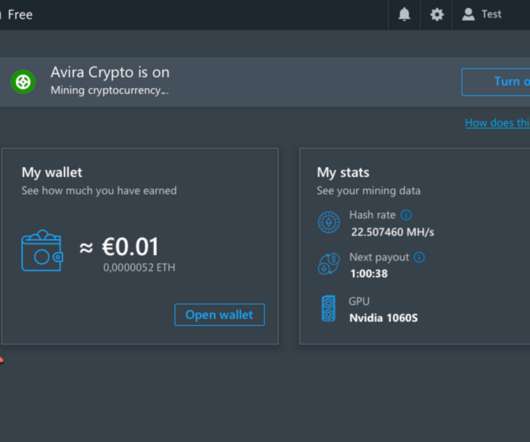
500M Avira Antivirus Users Introduced to Cryptomining
Krebs on Security
JANUARY 8, 2022
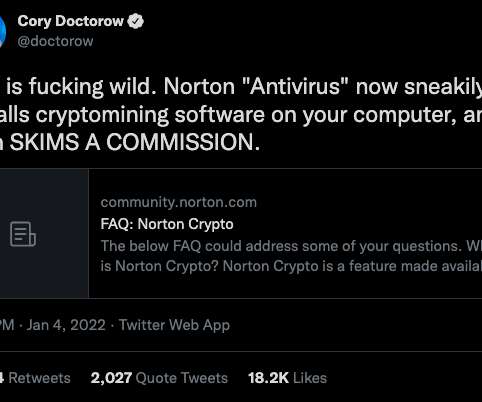
Many readers were surprised to learn recently that the popular Norton 360 antivirus suite now ships with a program which lets customers make money mining virtual currency. KG is a German multinational software company best known for their Avira Free Security (a.k.a. Avira Free Antivirus). Avira Crypto. based NortonLifeLock Inc.,







































Let's personalize your content