CrowdStrike 2025 Global Threat Report: 51-Second Breaches Shake Cybercrime
eSecurity Planet
MARCH 3, 2025
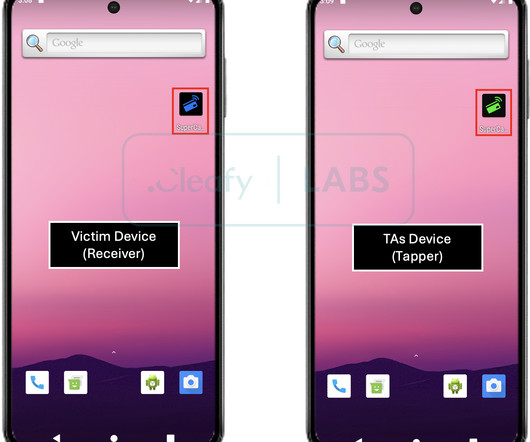
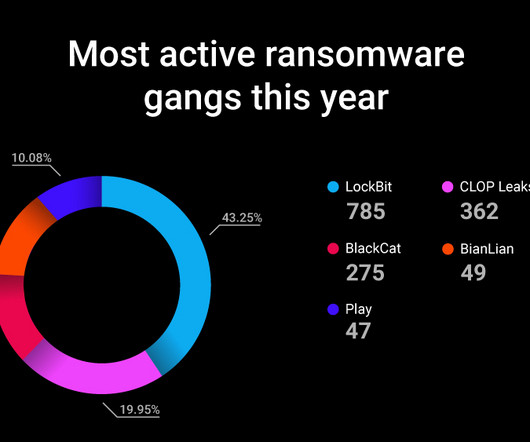
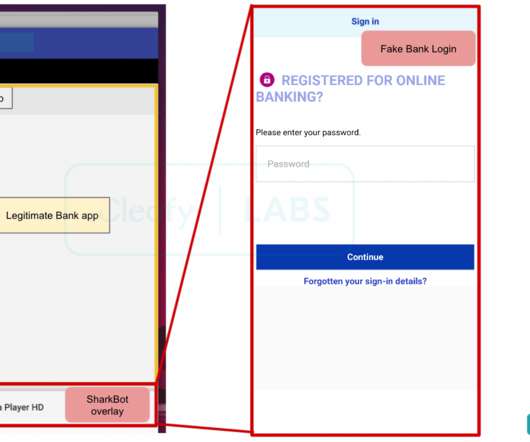
Notably, 79% of detections were malware-free a reminder that modern adversaries often bypass traditional antivirus defenses by leveraging innovative, non-malware techniques. The business of cybercrime Cybercriminals are no longer disorganized hackers. Evolving tactics in a digital world: should you care?

















































Let's personalize your content