Microsoft has taken legal and technical action to dismantle the Zloader botnet
Security Affairs
APRIL 13, 2022
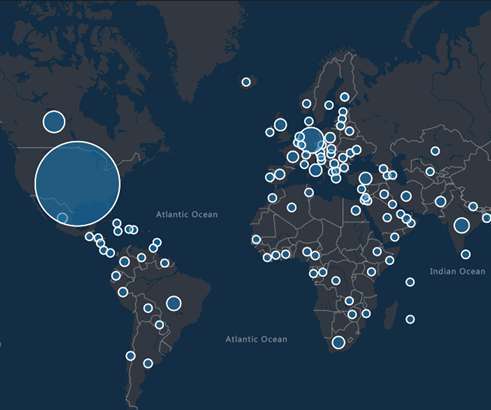
Microsoft dismantled the C2 infrastructure used by the ZLoader trojan with the help of telecommunications providers around the world and cybersecurity firms. Microsoft’s Digital Crimes Unit (DCU) announced to have shut down dozens C2 servers used by the infamous ZLoader botnet. ” reads the report published by Microsoft.
















Let's personalize your content