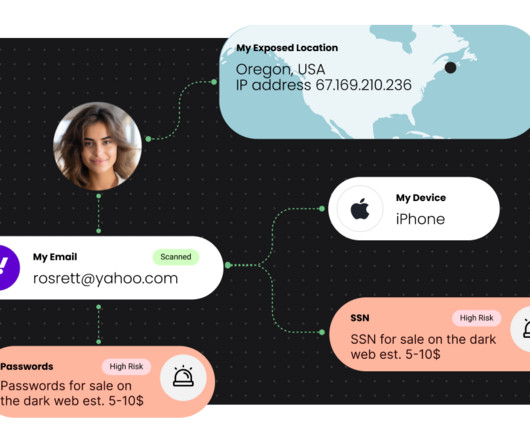
Introducing the Digital Footprint Portal
Malwarebytes
APRIL 10, 2024
Digital security is about so much more than malware. When I started Malwarebytes more than 16 years ago, malware was the primary security concern—the annoying pop-ups, the fast-spreading viruses, the catastrophic worms—and throughout our company’s history, Malwarebytes routinely excelled against this threat. It was our attitude.























Let's personalize your content