Becoming an MSSP: Tools, Services & Tips for Managed Security Services
eSecurity Planet
FEBRUARY 9, 2022
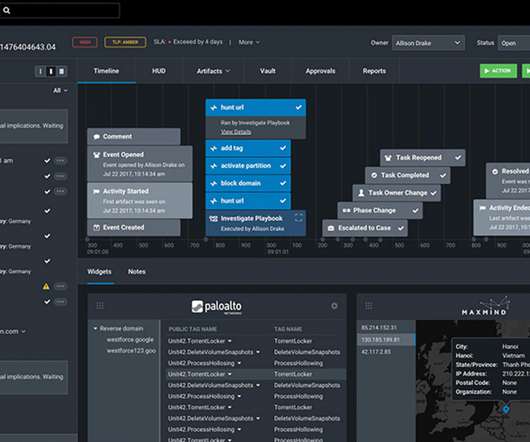
54% of ESG respondents stated that the primary drivers behind technology spending were strengthening of cybersecurity and improving resiliency against attacks. Phishing , general malware , and Distributed Denial of Service ( DDoS ) attacks are more common. Security is quite different from other areas of IT.






























Let's personalize your content