Experts link the Black Basta ransomware operation to FIN7 cybercrime gang
Security Affairs
NOVEMBER 3, 2022
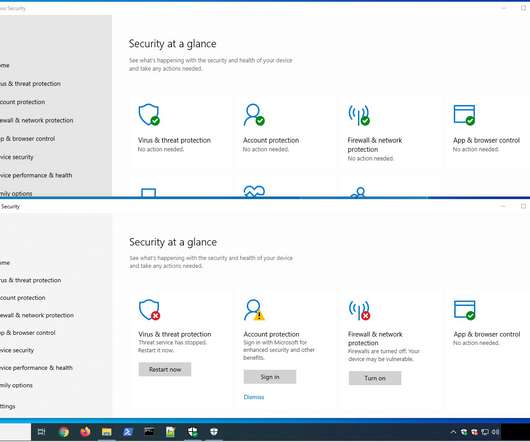
The Sentinel Labs’s analysis revealed that Black Basta ransomware operators develop and maintain their own toolkit, they documented only collaboration with a limited and trusted set of affiliates. The DisableAntiSpyware parameter allows disabling the Windows Defender Antivirus in order to deploy another security solution.
























Let's personalize your content