Giant health insurer struck by ransomware didn't have antivirus protection
Malwarebytes
OCTOBER 11, 2023
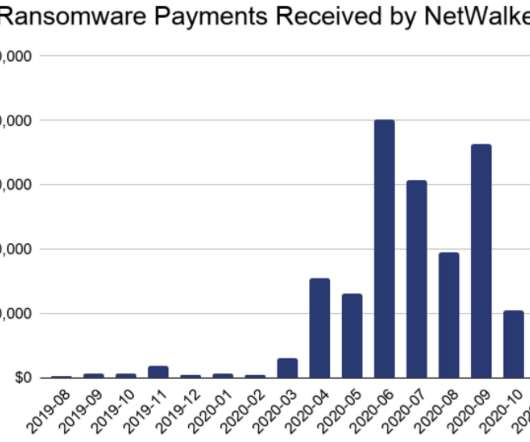
The Philippine Health Insurance Corporation (PhilHealth), has confirmed that it was unprotected by antivirus software when it was attacked by the Medusa ransomware group in September. How to avoid ransomware Block common forms of entry. Detect intrusions. Test them regularly to make sure you can restore essential business functions swiftly.































Let's personalize your content