Cisco Confirms Data Breach, Hacked Files Leaked
Dark Reading
AUGUST 11, 2022
Ransomware gang gained access to the company's VPN in May by convincing an employee to accept a multifactor authentication (MFA) push notification.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.
Dark Reading
AUGUST 11, 2022
Ransomware gang gained access to the company's VPN in May by convincing an employee to accept a multifactor authentication (MFA) push notification.

IT Security Guru
OCTOBER 26, 2023
Enter Two-Factor Authentication, or 2FA for short. Here’s a shocking stat: according to the Verizon Data Breach Investigations Report , 81% of hacking-related breaches leverage either stolen or weak passwords. Always use VPN for your safety to protect your data from prying eyes. What Exactly is 2FA?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Hot for Security
MARCH 29, 2021
Have you ever wondered why your email address and other information appeared in a data breach impacting a platform you never signed up for? and River City Media data breaches. Who is Verifications.io, and what information was exposed in the data breach? Was your personal data exposed in a data breach?

Cisco Security
AUGUST 24, 2023
Cisco is aware of reports that Akira ransomware threat actors have been targeting Cisco VPNs that are not configured for multi-factor authentication to infiltrate organizations, and we have observed instances where threat actors appear to be targeting organizations that do not configure multi-factor authentication for their VPN users.

Security Affairs
APRIL 28, 2024
From March 18, 2024, to April 16, 2024, Duo Security and Cisco Talos observed large-scale brute-force attacks against a variety of targets, including VPN services, web application authentication interfaces and SSH services.

Security Affairs
FEBRUARY 16, 2024
The threat actor compromised network administrator credentials through the account of a former employee that was used to successfully authenticate to an internal virtual private network (VPN) access point. The threat actor likely obtained the employee’s account credentials from a third-party data breach.

Thales Cloud Protection & Licensing
OCTOBER 28, 2021
Trick or Treat: The Choice is Yours with Multifactor Authentication. Whether you want the ‘trick’ of a malevolent threat actor infiltrating your network by exploiting a compromised password or the ‘treat’ from the peace of mind associated with multifactor authentication, the choice is yours. Fri, 10/29/2021 - 05:29.

Security Affairs
OCTOBER 21, 2023
Okta says that threat actors broke into its support case management system and stole authentication data, including cookies and session tokens, that can be abused in future attacks to impersonate valide users. HAR files can also contain sensitive data, including authentication information. ” concludes the advisory.

The Last Watchdog
MARCH 6, 2021
Set-up 2-factor authentication. If somehow passwords are leaked, a hacker can cause a data breach. Two-factor authentication or two-step verification involves adding a step to add an extra layer of protection to accounts. A two-factor verification helps in protecting from a cybersecurity breach.

Security Affairs
JANUARY 13, 2024
” The ransomware attack reported in late 2023, targeted organizations’ networks using poorly secured VPN gateway on Cisco ASA or FTD devices. Rapid7 researchers, they noticed that threat activity targeting Cisco ASA SSL VPN appliances dates back to at least March 2023.

Malwarebytes
FEBRUARY 19, 2024
The attacker managed to authenticate to an internal virtual private network (VPN) access point, further navigate the victim’s on-premises environment, and execute various lightweight directory access protocol (LDAP) queries against a domain controller. Use phishing-resistant multifactor authentication (MFA).

Security Affairs
JANUARY 13, 2024
Akira ransomware targets Finnish organizations GitLab fixed a critical zero-click account hijacking flaw Juniper Networks fixed a critical RCE bug in its firewalls and switches Vast Voter Data Leaks Cast Shadow Over Indonesia ’s 2024 Presidential Election Researchers created a PoC for Apache OFBiz flaw CVE-2023-51467 Team Liquid’s wiki leak exposes (..)

Security Affairs
JULY 27, 2023
This would make it extremely complicated for the company to inform its clients about a data breach or to warn them of malware attacks,” researchers said. What DepositFiles data was exposed? The exposed file had credentials for the Redis database, allowing anyone to read, edit, or delete data stored there.

Security Affairs
JANUARY 13, 2024
” The ransomware attack reported in late 2023, targeted organizations’ networks using poorly secured VPN gateway on Cisco ASA or FTD devices. Rapid7 researchers, they noticed that threat activity targeting Cisco ASA SSL VPN appliances dates back to at least March 2023.

Security Boulevard
JULY 10, 2023
Public key infrastructure (PKI) offers a globally accepted standard for implementing various security protocols and authentication mechanisms. e-commerce and online banking), and authenticate the identity of an entity in an online environment. require PKI to ensure data security through authentication and non-repudiation mechanisms.
Cisco Security
AUGUST 4, 2021
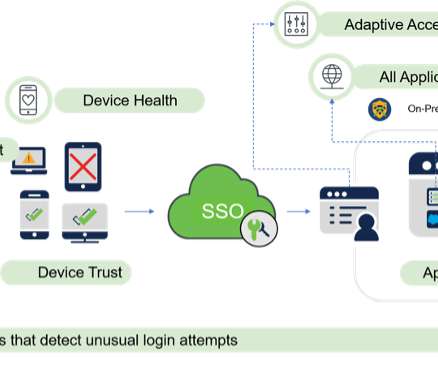
Zero Trust principles help protect against identity and access-based security risks by requiring all users, whether inside or outside the organization’s network, to be authenticated, authorized, and continuously validated for security configuration and posture checks before granted access to applications and data. LinkedIn.

Duo's Security Blog
FEBRUARY 16, 2022
Retail’s great “digital transformation” sped up, as did the number of data breaches impacting retail. The costs that follow a data breach are trending upward year over year. Data breach costs rose from $3.86 million, according to IBM and the Ponemon Institute’s Cost of Data Breach Report 2021.

Adam Levin
FEBRUARY 7, 2019
While the personal data of 4,557 students, or 2,800 Girl Scouts , or 3,000 Minnesotans might pale in comparison to the steady flow of mega breaches from the likes of Equifax or Collection #1-5, but any of them have the ability to effectively sink a business financially.

Hot for Security
JUNE 22, 2021
If you do, chose password-protected networks and use a VPN to prevent eavesdropping on online activity Resist the urge to post on social media platforms about your activity and location. The dedicated browser and VPN will protect your online presence, providing safe online banking and shopping by encrypting traffic on your smart devices.

CyberSecurity Insiders
APRIL 16, 2021
Organizations with weak cybersecurity have been severely punished with cyber-attacks, data breaches, and huge losses in the past. According to Varonis and RiskBased, over 4 billion records were illegally accessed through data breaches in 2019. Security through a VPN. Password managers and two-factor authentication.

Pen Test Partners
FEBRUARY 14, 2024
According to the 2022 Verizon data breach incident report only 5% of data breaches investigated by them were caused by software vulnerabilities. However, the same report shows that the human element accounted for 74% of data breaches. Well, it looks like people have finally got good at patching.

Tech Republic Security
JULY 18, 2023
Use this comprehensive list of strategies to help you safeguard your company's data from threats and data breaches.

Security Affairs
SEPTEMBER 12, 2022
Upon achieving an MFA push acceptance, the attacker had access to the VPN in the context of the targeted user. The attacker ultimately succeeded in achieving an MFA push acceptance, granting them access to VPN in the context of the targeted user. .

SecureList
NOVEMBER 23, 2023
VPN services on the rise A VPN creates an encrypted tunnel that effectively conceals user traffic from internet service providers and potential snoopers, thus reducing the number of parties that can access user data even on public Wi-Fi.

Security Boulevard
JULY 19, 2023
Particularly in the workplace, staff can become overwhelmed with security warnings, IT alerts, cybersecurity policy documents, password change requests, or even media consumption of stories about data breaches at other companies. The financial risk According to IBM , the average cost of a data breach in the U.S.

Duo's Security Blog
MAY 18, 2021
Verizon just released its 14th edition of the Verizon Data Breach Incident Report (DBIR) covering 2020’s foray into cybersecurity. The DBIR states that phishing, ransomware, web app attacks dominated data breaches in 2020. It’s fair to say that 2020 was impossible to predict, but had a significant impact.

CyberSecurity Insiders
APRIL 1, 2021
The consequences of a data breach can vary greatly depending on the intention of the adversary. The 2020 Global State of Industrial Cybersecurity report found that 74% of IT security professionals are more concerned about a cyberattack on critical infrastructure than an enterprise data breach. Multi-Factor Authentication.

Spinone
DECEMBER 20, 2018
How can organizations reduce, prevent, and even avoid data breaches in the cloud? Let’s look at a few strategies and technologies that can be successfully used to secure data in the cloud and help reduce and even prevent data breaches in the cloud. Often, however, it is not in a good context.

Security Affairs
NOVEMBER 29, 2020
A cyberattack crippled the IT infrastructure of the City of Saint John Hundreds of female sports stars and celebrities have their naked photos and videos leaked online Romanians arrested for running underground malware services Threat actor shared a list of 49,577 IPs vulnerable Fortinet VPNs Computer Security and Data Privacy, the perfect alliance (..)

Duo's Security Blog
JUNE 2, 2021
This report Bridging Healthcare Security Gaps: Better Authentication Improves Controls aims to bring clarity and solutions to these security gaps. In this report you will learn: About zero trust and how multi-factor authentication meets the HIPPA requirements for a third factor of authentication.

CyberSecurity Insiders
DECEMBER 6, 2022
When employees aren’t in the office, they’re liable to engage in risky behaviors such as using unsecured WiFi without a VPN, leaving work devices unlocked in public places, and clicking on malicious emails. Companies should also provide clear channels for reporting suspicious incidents. The average American household has 22 connected devices.

IT Security Guru
MARCH 28, 2023
Having a cybersecurity plan ensures that you remain protected against data breaches, phishing scams , and other cybercrimes. On top of that, turn on two factor authentication. Use a VPN Using a VPN is essential when working with sensitive data or files.

Security Affairs
MAY 9, 2021
Experts found critical authentication bypass flaw in HPE Edgeline Infrastructure Manager UNC2529, a new sophisticated cybercrime gang that targets U.S.

Krebs on Security
MAY 19, 2020
In January 2019, dozens of media outlets raised the alarm about a new “megabreach” involving the release of some 773 million stolen usernames and passwords that was breathlessly labeled “the largest collection of stolen data in history.” “ Sanixer “) from the Ivano-Frankivsk region of the country.

Krebs on Security
JULY 10, 2022
“I was able to answer the credit report questions successfully, which authenticated me to their system,” Turner said. That’s because Experian does not offer any type of multi-factor authentication options on consumer accounts. But now he’s wondering what else he could do to prevent another account compromise.
Security Affairs
MAY 11, 2023
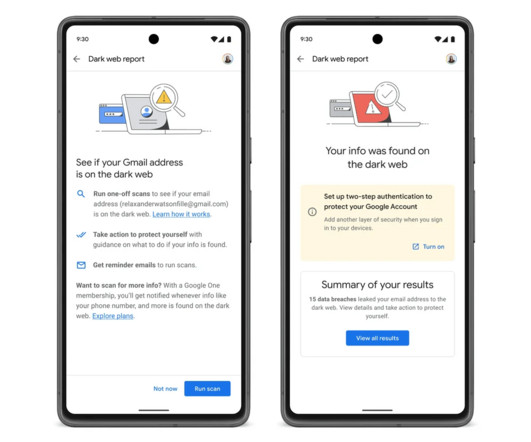
Once an email address is discovered on the dark web, Google will urge users to enable two-step authentication (2FA) to protect their Google accounts. Google also announced the availability of VPN access for all Google One plans. The upcoming feature will be also extended to users from select international markets.

SC Magazine
JUNE 3, 2021
A follow-up investigation by Mandiant found that the hackers did not gain access to the systems that control the trains, and MTA officials said rider safety was not at risk and the personal data of riders was not compromised. . The attackers used the access to plant web shells on the VPN servers in MTA’s environment.

Duo's Security Blog
AUGUST 24, 2022
estimated that 44% of educational institutions were targeted by ransomware attacks in 2020 — more data breaches than we’d ever seen in prior years. Thankfully, the government is responding with new laws and cybersecurity compliance revisions in hopes to educate, fund and bolster data security initiatives in K-12.

Webroot
FEBRUARY 15, 2024
If you’ve been compromised in a data breach, hackers can use your stolen email and password to try and enter thousands of other sites—and if you keep using the same credentials, they’ll be successful. Use two-factor authentication Two-factor authentication adds an extra layer of security to your online accounts.

eSecurity Planet
AUGUST 22, 2023
The technologies for secure remote access can range from VPNs and multi-factor authentication to more advanced access and zero trust controls. As the internet has enabled us to access work, data, and equipment from any location, remote access security has become increasingly crucial.

Thales Cloud Protection & Licensing
MAY 10, 2022
All companies are subject to state-specific data breach laws for collecting, processing, and storing personal data. You can ensure insurance coverage and even reduce premiums if you are implementing good cyber security practices - starting off with multi-factor authentication – in order to avoid a breach.

CyberSecurity Insiders
DECEMBER 18, 2021
Use Strong Passwords & Two-Factor Authentication. If your password is exposed in a data breach, you must change it immediately. Websites might inform you via e-mail when such breaches occur, but with a considerable delay. Standard passwords from manuals are prime targets for cyberattackers.

SecureWorld News
JULY 27, 2021
Ensure that old VPN remote access systems are taken down when new ones are instituted.". Ensure that when it comes to a private company that holds an effective monopoly and a bottleneck over critical infrastructure with national security implications, that company does not use VPN remote access with lax security measures.".

CyberSecurity Insiders
SEPTEMBER 14, 2021
This does not bode well for their longevity, as other industry data shows that 60% of small businesses that suffer a data breach will be out of business within six months. Use of a VPN – virtual private networks (VPN) create a secure connection to other networks over the internet.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content