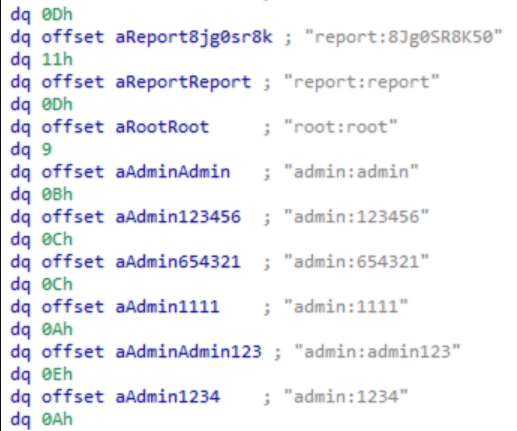
AT&T Alien Labs finds new Golang malware (BotenaGo) targeting millions of routers and IoT devices with more than 30 exploits
CyberSecurity Insiders
NOVEMBER 11, 2021
Deployed with more than 30 exploits, it has the potential of targeting millions of routers and IoT devices. However, there is a difference between the Mirai malware and the new malware variants using Go, including differences in the language in which it is written and the malware architectures. It also has different DDoS functionality.



















Let's personalize your content